While the continuous adoption of new IT and OT technologies for business certainly brings improved productivity, it also introduces new security risks. As cybercrime increasingly becomes professionalised, so too do cyber threats rapidly become more sophisticated, subtle, and numerous. Furthermore, hackers relentlessly refine their techniques and develop new workarounds against today’s most advanced cybersecurity solutions.
These factors combined create a cyber threat landscape wherein organisations face unprecedented and more dangerous threats than ever before. To put this into perspective, the number of cyberattacks rose in 2022 by 38 per cent over the previous year.
However, not all cyber threats are made equal; some stand the test of time, while others come and go from year to year. For 2023, businesses should be prepared to face the following critical cybersecurity challenges.
Zero-day vulnerabilities in supply chains
Zero-day vulnerabilities, previously unknown software vulnerabilities overlooked by the vendor of the target software, pose a temporary yet significant risk to corporate cybersecurity. Until these vulnerabilities are patched out or even discovered in the first place, hackers can freely exploit them to adversely affect computers, programs, data, and even entire networks. But even when a patch is made available, some companies do not immediately install them for various reasons.
One area where zero-day attacks are concerning is in the software supply chain. It is increasingly common for companies to lack total visibility over their applications’ third-party, open-source code. Should these external libraries have unpatched vulnerabilities, it is only a matter of time before cybercriminals exploit them. Moreover, vulnerable and widely used libraries create potential attack vectors against countless organisations.
Weaponisation of legitimate tools
Nowadays, there is a fine line between malware, legitimate system administration, and pen testing tools. Oftentimes, functionalities that hackers would build into their malware already come included in the operating systems of their targets or are available in legitimate security tools that will unlikely be seen as malware by detection tools.
Hackers have increasingly taken advantage of such opportunities in their attacks since they have a much lower chance of getting detected by leveraging legitimate tools and built-in features in their attacks. Furthermore, using existing solutions helps scale their attack campaigns and upgrade to more state-of-the-art hacking tools.
Ransomware
Ransomware is malicious software that blocks access to computer systems and data until a ransom is paid off. Since there are no guarantees that the hackers will fulfil their promise of returning access, there is a chance that victims may lose both their data and a huge sum of money if they are ever hit with ransomware. However, by following the best practices in making data backups, they could potentially mitigate the damage of a ransomware attack.
Hackers can also opt to launch double extortion attacks that include data theft on top of data encryption or just go with the former, making it a data breach attack. Ransomware data breaches are faster, harder to detect, and cannot always be resolved with data backups, making them a more lucrative attack for hackers.
Destructive malware or wipers
Although data breaches and ransomware are the most prevalent threats to an organisation’s data security, destructive malware and wipers can cause even greater negative impacts. This is because, as their name suggests, these types of malware delete the victim’s data entirely instead of being encrypted or held ransom.
Wipers have risen in popularity as of 2022, with multiple families of the malware being deployed against Ukraine, most likely by Russian threat actors as part of their ongoing conflict. Other countries like Albania and Iran have also suffered destructive cyberattacks of similar nature, which indicates its increasing popularity as a tool for cyberwarfare and hacktivism.
Third-party risk in the cloud
The adoption of cloud computing on the rise also brings more significant security implications to consider. Lack of familiarity with the best practices in cloud security, cloud shared security model, and various other factors can make cloud environments more vulnerable than on-site infrastructure.
Although hackers are increasingly targeting cloud infrastructures, a more concerning rising trend is their targeting of cloud service providers. Since these entities work with countless organisations, they are essentially a goldmine for valuable, sensitive customer data and even their individual clients’ IT infrastructure. Exploiting the trust relationships between businesses and their cloud service providers allows attackers to dramatically increase the impact and scale of their attacks.
Tips for Dealing With the Cybersecurity Challenges of 2023
Keep these considerations in mind when designing and upgrading your cybersecurity architecture to address the challenges above.
-
Prevention-focused security
Many of today’s corporate cybersecurity strategies are detection-focused, a responsive approach that only deploys their security solutions and personnel once an ongoing threat is identified to mitigate or remediate its effects. This gives attackers a window to launch their attack before it is eventually addressed, which is enough of an opportunity to cause damage and entrench their foothold, making remediation more challenging and expensive.
Thus, it is better to focus on preventing these attacks from happening in the first place by identifying and blocking inbound them before they ever reach their target. The result is a complete avoidance of the potential threat, damage, and cost it may have incurred.
-
Security consolidation
Since cyber threats evolve in combat increasingly effective cybersecurity solutions, companies cannot afford to lag in adapting the latter’s developments to better protect against advanced attacks.
However, implementing these capabilities through specialised yet standalone solutions can do more harm than good, making it more challenging to configure, monitor, and operate a cybersecurity infrastructure.
It is therefore recommended for organisations to leverage security consolidation instead. This entails deploying a single security platform with all the required security features to significantly improve the effectiveness and efficiency of a security architecture and its personnel, enhancing threat management capabilities.
-
Comprehensive Protection
The increasing complexity of corporate IT architectures provides hackers with countless potential avenues of attack. Remote work, the Internet of Things, and cloud computing are examples of new technologies that introduce new security risks and vulnerabilities that hackers can exploit to gain unauthorised access. A robust cybersecurity posture means having comprehensive coverage and protection against as many potential attack vectors as possible.
A good first step towards this goal is adopting operational technology (OT) security that protects the various elements involved in daily operations in conjunction with conventional IT cybersecurity. One example of the many parts that make up OT security is one-way data diode in Singapore, such as ST Engineering Data Diode. This solution (also known as a one-way firewall) eliminates the risk of data leaks and external interference by using unidirectional transmission between an organisation’s physical networks connected to its own other networks or the external Internet.
Conclusion
The cyber threat landscape constantly evolves in response to IT/OT architecture changes and advancing security solutions. As such, managing corporate and industrial cybersecurity risk warrants deploying defences against known and unknown threats.
To better protect your manufacturing organisation, get in touch with us at Allied Solutions today and let our veteran team of experts help you find the tailored cybersecurity solutions that best meet your industrial needs. For more details about how our products, such as GE Proficy Historian and Parsec’s TrakSYS software, and services can enhance your business processes, drop us a message anytime.
As the world becomes increasingly interdependent and complex, it has likewise become incredibly hard to provide a product or service without a supply chain. However, this dependency creates extra risks – from significant business disruptions to reputational losses. In 2021, for instance, numerous organizations were affected by supply chain cyberattacks that can result in system downtimes, financial losses, and reputational damage.
For this reason, it is important for companies or organizations to improve the way they manage supply chain risks by adopting more robust practices for cyber risk management.
With nearly all business interactions and processes going digital, cybersecurity is the key to stable and safe supply chain operations. Read on to discover some of the best practices for cyber risk management that every business should embrace to protect their supply chain processes.
1. Perform a risk assessment
Before taking any action to improve the security of your supply chain, it is necessary to evaluate possible risks. To do so, you must understand your supply chain and determine its crucial components. Identify who your suppliers are and analyze their level of cybersecurity. For this purpose, it may be helpful to group vendors into various risk profiles, prioritizing every third party according to their vulnerability level, impact on your business, and access to your data and systems.
Figure out the weakest points in your supply chain, and determine whether you can supplement these suppliers or ask them to enhance their security. Aside from individuals and organizations in your supply chain, be aware of the safety of all hardware and software products supplied to you. To have a better overview of the risks, you can illustrate a tree of all interactions between your company and supply chain elements. This will help you monitor connections and visualize supply chain risks.
2. Secure your data
The way significant business is gathered, processed, and stored is essential when it comes to supply chain security. Because of this, you need to have effective network security in place and secure your business data on several layers – from the separate applications utilized by your company to the entire infrastructure. Try to improve your cybersecurity by using data protection technologies, such as tokenization, encryption, and data diodes.
In Singapore, data diodes are a fail-safe way to secure confidential data and protect sensitive systems. Specifically, data diodes by ST Engineering are used in numerous industries in the country and around the world because they come with an extensive range of advanced cybersecurity solutions, including endpoint security and threat intelligence, that effectively minimize the risk of data breaches and monetary losses in business. To avoid significant losses, be sure to secure data management not just within your company but across the infrastructures of all your suppliers.
3. Collaborate with your suppliers to enhance security
It is difficult to maintain a secure supply chain if you do not have close collaboration with your suppliers. Maintaining clean communication with your suppliers on a regular basis is vital for preventing supply chain vulnerabilities. You can schedule gatherings or visits dedicated to enhancing supply chain security and resilience, as well as carry out training to raise awareness among third parties.
It is necessary to communicate your security standards and needs to your suppliers and look for ways to make them uniform throughout your whole supply chain. To outline duties in your collaboration with third parties, you should consider utilizing service-level agreements (SLAs), which can assist you in communicating and standardizing requirements among your suppliers. SLAs can also make your suppliers accountable for cybersecurity incidents that might be caused by them.
4. Monitor the activities of your suppliers
To minimize the possibility of a malicious insider attack in your company, consider putting in place constant activity monitoring for your suppliers and other supply chain entities that access your system. By monitoring all external users accessing your network, you can increase the accountability of your suppliers and enable efficient investigation in case of an attack. Moreover, monitoring of third-party activity is a common requirement in IT compliance.
To monitor the activities of your suppliers for security and efficiency purposes, you may invest in a reliable manufacturing scheduling software like Parsec’s TrakSYS software. TrakSYS is a trusted production planning and scheduling platform that is equipped with various tools to streamline the operations of an organization. It acts as a calendar that details every component of a production cycle, and this schedule encourages accountability and on-time accomplishment of key tasks.
5. Build an incident response plan
No matter how much you try to protect your systems, risks in the supply chain are sometimes simply inevitable. Because of the unforeseen nature of these risks, it is essential to expect that your systems will be compromised at any time and establish defences so that in the event that a third-party-related incident occurs, you will be prepared completely.
Based on the results of your risk assessment, come up with a thorough incident response plan for your security teams. This plan must include roles, procedures, and conditions of responses to a potential security incident. If a security attack occurs outside your perimeter, it is important to provide assistance to a third party in reducing the consequences because supply chain security is your security too.
Conclusion
The numerous advantages of supply chains come at the price of risks presented to each entity in the supply chain, particularly cybersecurity risks. Due to the tight interconnection in the supply chain, it raises the possibility of different kinds of attacks, such as supply chain attacks, third-party attacks, and destructive activities inside your company. Hence, you need to strengthen the security of your supply chain and make it less vulnerable to potential threats by following the best cyber risk management practices enumerated in this article.
If you are looking to make your data more secure and improve the protection and efficiency of your supply chain operations, Allied Solutions is the industry expert that can help you! Allied Solutions provide the most excellent automation systems and industrial manufacturing systems that can effectively optimize every aspect of a supply chain, such as data diodes and many more. Do not hesitate to contact us today to learn more about our products and services.
With the increasing frequency and severity of cyberattacks in recent years, organizations across all sectors have placed their cybersecurity as their topmost priority, especially those in the manufacturing industry. This is no surprise seeing as approximately 90% of manufacturing companies suffered some form of cyberattack on their production or energy supplies in 2021.
That being said, improving operational technology (OT) cybersecurity is easier said than done due to the many technical, operational, and investment obstacles of such an endeavor. Regardless, as the world becomes increasingly more digital, industrial organizations must find a way to overcome these barriers and make progress in securing their OT environments.
These are the signs to look out for that indicate your OT cybersecurity posture may be outdated and needs to be upgraded immediately.
1. Unsupported or outdated operating systems
Today, countless OT devices embedded with unsupported or outdated operating systems, like Windows 7, Windows XP, and even Windows 95, can still be found in many modern OT environments. This is because many OT systems and devices were developed way back when devices were still air-gapped, and things like authentication, encryption, and cybersecurity were not much of a concern.
A recent report from Microsoft further supports the prevalence of this issue, as it is estimated that 71% of OT systems have unsupported or outdated operating systems, while 66% no longer have automatic updates. Unfortunately, not much can be done about these embedded systems unless the vendors that built them do not upgrade. And even if they could do so, there would be a significant cost from the downtime involved in replacing these outdated systems and processes.
2. Weak or insecure passwords
Legacy software found in many dated OT devices comes with many shortcomings from a modern perspective, including the lack of stronger authentication. However, operators familiar with these devices do not often see this as a problem since insecure passwords provide convenient entry to the networks they need to access to do their jobs.
However, this also makes it easy for cybercriminals to gain unauthorized access by guessing or brute-forcing their way in. Earlier this year, the Cybersecurity and Infrastructure Security Agency warned that hackers were accessing internet-exposed uninterruptible power supply devices because they were still using default usernames and passwords.
To prevent cybercriminals from gaining unauthorized access to critical OT assets, consider adopting protective measures like OPSWAT OTFUSE™, an industrial IDS/IPS appliance that protects PLCs and other key devices by applying highly granular device access policies and enforcing device access zones.
3. Using traditional means of risk assessment
Another glaring issue with organizations using older OT cybersecurity is the design of their risk assessment. The traditional method starts with determining risks through a survey-based approach and reviewing the data from IT management databases. The data is then evaluated to create a roadmap of initiatives that must be completed over time.
This way is appropriate in many IT environments since the initiatives are done centrally, but it poses significant problems when extended into a distributed industrial environment. First, survey-based assessments in ICS/OT environments generally lead to insufficient practical information for many reasons, such as lack of systems management data, personnel on-site typically do not know the answers to the questions, etc. This leads to a lacking foundation to go on.
Second, remediation is not an enterprise solution. More often than not, each facility or site requires a unique patching approach depending on their devices, configuration hardening, etc. Keep in mind that many environments do not operate from a central active directory server, which means enterprise solutions will require local deployments, leading to a substantial lag between assessment and remediation.
Conclusion
As operational technology becomes more cloud-managed and internet-facing, industrial sectors become more exposed to threats that could lead to more devastating consequences than IT data breaches. Given the inherent cybersecurity vulnerabilities of many OT systems, it is imperative to look for the signs yours may need to be updated sooner than later.
If it is time to improve your OT cybersecurity, Allied Solutions can help you achieve your security posture goals. We deliver cost-effective turnkey solutions that meet your operational needs, including OPSWAT’s IT and OT critical infrastructure cybersecurity solutions designed to elevate your OT security posture. To learn more about our other products, such as Parsec’s TrakSys Software, GE Proficy Historian, and more, don’t hesitate to contact us today.
Some Key Features of ST Engineering Data Diode
Information Assurance by Design
- Ensures no data leakage. Separate power supply to mitigate against side-channel attacks
- Certified under Common Criteria (CC EAL4+) and NITES by CSA.
High Throughput and Robust Performance
- Files lost detection capability.
- Configurable for High Availability.
Ease of System Integration and Customisation
- Supports an array of IT, IoT and ICS/SCADA networking protocols for system integration and interoperability.
Compact Design
- Allows all functionalities to be encapsulated within a compact footprint.
Our Holistic Solution for OT & IT Networks
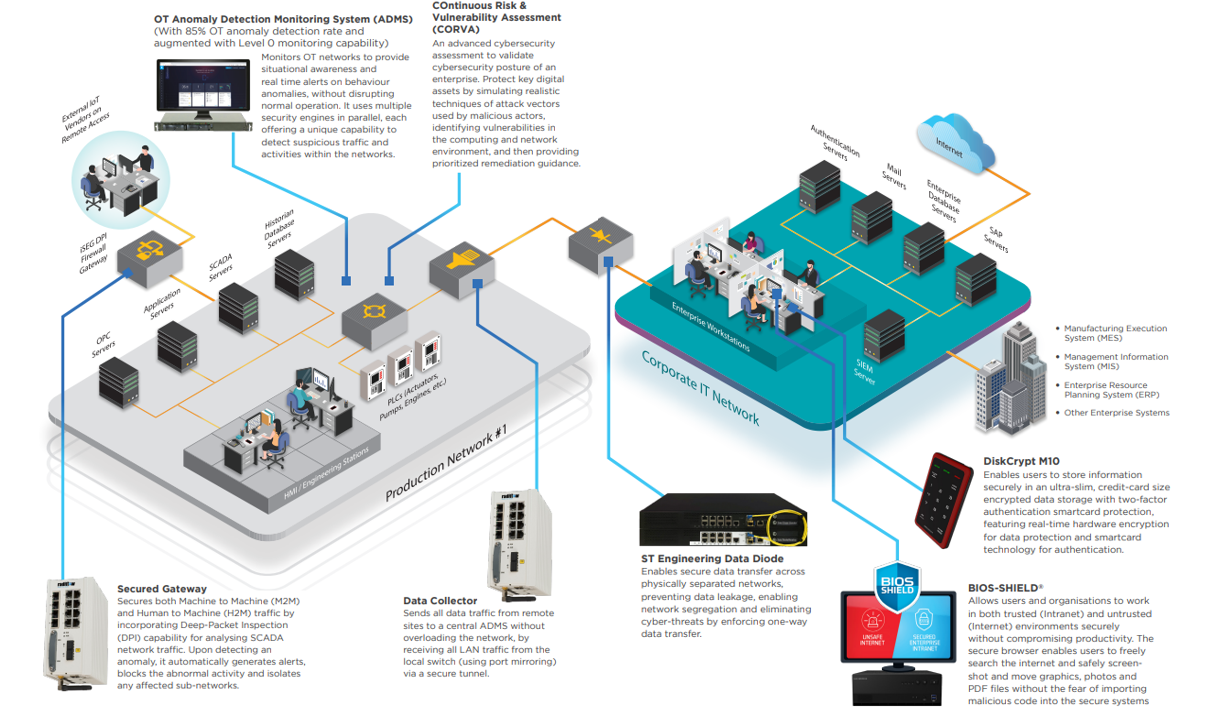
Our holistic cybersecurity solution for Production OT networks and Enterprise IT is designed for CII, which includes Building Management System, ensuring the cybersecurity of ICS and SCADA systems.
Embracing security by design, our end-to-end solution suite involves the main deployment of OT Anomaly Detection Monitoring System (ADMS), Continuous Risk & Vulnerability Assessment (CORVA), Data Collector (DC), and Secured Gateway (SG), along with proprietary products such as Data Diode, Diskcrypt M10, and BIOS-SHIELD®
Radiflow’s OT Visibility and Anomaly Detection & Secure Gateways
Radiflow specializes in solutions for industrial automation networks namely taking the guesswork out of OT security with products such as OT Visibility and Anomaly Detection & Secure Gateways.
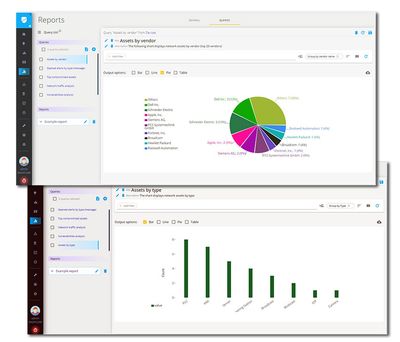
OT Visibility and Anomaly Detection
Solution Suite for Threat Detection & Monitoring
Proactive cybersecurity non-intrusive monitoring of distributed production networks for changes in topology and behavior.
Secure Gateways
OT Security for Remote Sites and Substations
Secure Gateways featuring DPI firewall, work order-based technician access to assets and system-wide management tool

Keeping OT & IT Network Cyber Secure
Integration Benefits
- Ensures unidirectional (physical layer one-way) data transfer to protect critical OT systems.
- Supports all OPC UA built-in data types.
- Configures with KEPServerEX Automatic Tag Creation.
- Real-time without data loss:
- Real-time value update based on subscription
- Periodically queries of every monitored node’s values with re-transmit to ensure no loss
- Broad range device integration with more than 150 device drivers, client drivers, and advanced plug-ins

Some Key Features of ST Engineering Data Diode
Information Assurance by Design
- Ensures no data leakage. Separate power supply to mitigate against side-channel attacks
- Certified under Common Criteria (CC EAL4+) and NITES by CSA.
High Throughput and Robust Performance
- Files lost detection capability.
- Configurable for High Availability.
Ease of System Integration and Customisation
- Supports an array of IT, IoT and ICS/SCADA networking protocols for system integration and interoperability.
Compact Design
- Allows all functionalities to be encapsulated within a compact footprint.
Machine Learning and Analytics: Process Engineers Don’t Have to Be a Data Scientist
It has never been easy for any industrial organization taking on a digital transformation jersey including machine learning and analytics.
With proven processes and software technologies namely GE Digital’s Proficy CSense, the journey to success with machine learning and analytics become achievable for every industrial organization.
Process engineers have exceptional domain expertise to put together process models – or Process Digital Twins – and be able to interpret the models. This is the foundation for improving competitive advantage and success with analytics.
To drive analytics and improve processes, process engineers can align domain expertise to five capabilities:
1. Analysis
Automatic root cause identification accelerates continuous improvement
2. Monitoring
Early warnings reduce downtime and waste
3. Prediction
Proactive actions improve quality, stability, and reliability
4. Simulation
What-if simulations accelerate accurate decisions at a lower cost
5. Optimization
Optimal process setpoints improve throughput at acceptable quality by up to 10%




